1. RTFM
https://docs.gitlab.com/omnibus/
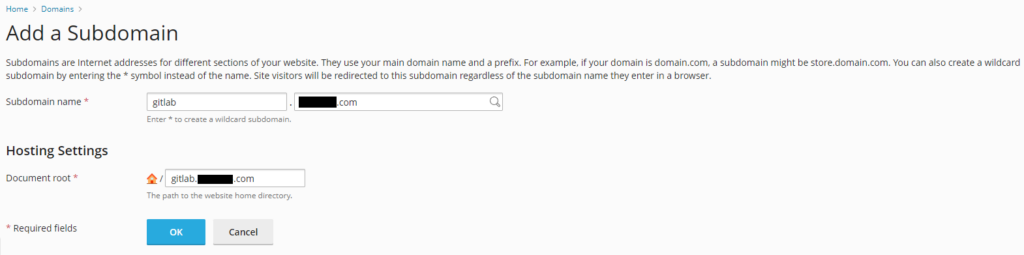
2. Create a Subdomain for your GitLab
- Plesk > Domains > Add Subdomain > gitlab.mydomain.com
3. Add additional configuration to your subdomain
- Plesk > gitlab.mydomain.com > Hosting & DNS > Apache & nginx Settings
3.1 Additional directives for HTTP
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteCond %{REQUEST_URI} !^/.well-known/.*
RewriteRule ^/(.*) https://%{HTTP_HOST}/$1 [last,redirect=301]
3.2 Additional directives for HTTPS
DocumentRoot /opt/gitlab/embedded/service/gitlab-rails/public ProxyRequests Off ProxyPreserveHost On ProxyPass / http://127.0.0.1:8181/ nocanon # Ensure that encoded slashes are not decoded but left in their encoded state. # http://doc.gitlab.com/ce/api/projects.html#get-single-project AllowEncodedSlashes NoDecode <Location /> # New authorization commands for apache 2.4 and up # http://httpd.apache.org/docs/2.4/upgrading.html#access Require all granted # Allow forwarding to gitlab-workhorse ProxyPassReverse / </Location> # Apache equivalent of nginx try files # http://serverfault.com/questions/290784/what-is-apaches-equivalent-of-nginxs-try-files # http://stackoverflow.com/questions/10954516/apache2-proxypass-for-rails-app-gitlab RewriteEngine on # Forward all requests to gitlab-workhorse except existing files like error documents # and except the Let's Encrypt challenge RewriteCond %{DOCUMENT_ROOT}/%{REQUEST_FILENAME} !-f [OR] RewriteCond %{REQUEST_URI} ^/uploads/.* RewriteCond %{REQUEST_URI} !^/.well-known/acme-challenge/[0-9a-zA-Z_-]+$ [NC] RewriteRule .* http://127.0.0.1:8181%{REQUEST_URI} [P,QSA,NE] RequestHeader set X_FORWARDED_PROTO 'https' RequestHeader set X-Forwarded-Ssl on # needed for downloading attachments DocumentRoot /opt/gitlab/embedded/service/gitlab-rails/public # Set up apache error documents, if back end goes down (i.e. 503 error) then a # maintenance/deploy page is thrown up. ErrorDocument 404 /404.html ErrorDocument 422 /422.html ErrorDocument 500 /500.html ErrorDocument 502 /502.html ErrorDocument 503 /503.html # It is assumed that the log directory is in /var/log/httpd. # For Debian distributions you might want to change this to /var/log/apache2. LogFormat "%{X-Forwarded-For}i %l %u %t \"%r\" %>s %b" common_forwarded ErrorLog /var/log/apache2/gitlab_error.log CustomLog /var/log/apache2/gitlab_forwarded.log common_forwarded CustomLog /var/log/apache2/gitlab_access.log combined env=!dontlog CustomLog /var/log/apache2/gitlab.log combined
3.3 nginx Settings
- Proxy Mode enabled
- Smart static files processing disabled
4. Install Let’s Encrypt Certificates
- Domains > gitlab.mydomain.com > Dashboard > Security > SSL/TSL Certificates
5. Add the GiLab reposity by script
Installation instructions: https://docs.gitlab.com/omnibus/installation/
Installation script: https://packages.gitlab.com/gitlab/gitlab-ce/install
curl -s https://packages.gitlab.com/install/repositories/gitlab/gitlab-ce/script.deb.sh | sudo bash
6. Install the GitLab package
(and ensure your URL starts with https)
EXTERNAL_URL="https://gitlab.mydomain.com" apt-get install gitlab-ce
7. Edit the /etc/gitlab/gitlab.rb
(and check/alter/add the following lines using vi, vim or nano)
- Find your plesk_user: Plesk > Domains > gitlab.mydomain.com > Dashboard > Connection Info
external_url 'https://gitlab.mydomain.com' nginx['enable'] = false web_server['external_users'] = ['www-data', 'plesk_user'] web_server['group'] = 'psacln' gitlab_workhorse['listen_network'] = "tcp" gitlab_workhorse['listen_addr'] = "127.0.0.1:8181"
8. Apply changes
sudo gitlab-ctl reconfigure sudo gitlab-ctl restart
9. Get the status of your gitlab installation
Usage instructions: https://docs.gitlab.com/ee/update/package/#get-the-status-of-a-gitlab-installation
sudo gitlab-ctl status sudo gitlab-rake gitlab:check SANITIZE=true
10. get or set your gitlab-ce root password
sudo cat /etc/gitlab/initial_root_password sudo gitlab-rake "gitlab:password:reset[root]"
11. login as root
(an configure, manage, administrate, use your installtion)