Assuming that OpenVPN has already been set up on a server, we only need to edit the server.conf and install the telnet package. However, if we want to solve this more elegant, we install the package expect and write a script.
1. RTFM
https://openvpn.net/community-resources/management-interface/
2. Install the packages
sudo apt-get install telnet expect
3. Activate the OpenVPN management service port
Edit /etc/openvpn/server.conf and add follwing lines:
management localhost 7505
If you don’t find it set yet, send the client a ping every 10 seconds and assume that it will be disconnected after two minutes.
keepalive 10 120
4. Write your script
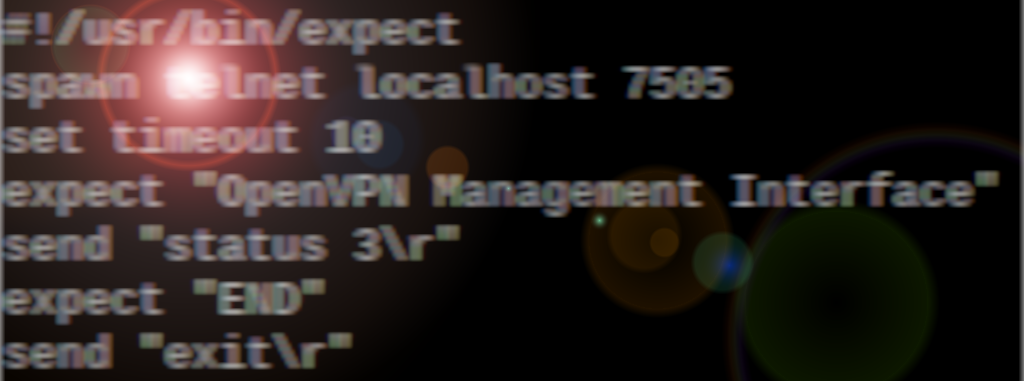
#!usr/bin/expect
spawn telnet localhost 7505
set timeout 10
expect "OpenVPN Management Interface"
send "status 3\r"
expect END
send "exit\r"
5. Further usage
Of course you can set up a monitoring, which would look like this:
white true; do ./openVPNuserlist.sh | grep -e ^CLIENT_LIST; sleep 1; done
On the other hand, you might get the idea that you could use the public IPv6 of a certain client in a whitelist or something, who knows. This could then be done with a follow-script:
#!/bin/bash
{ echo "allow " ; (/here/are/scripts/openVPNusers.sh | grep 'thewellknownclient*' | grep 'CLIENT_LIST' | awk '{print $3}') ; echo ";" ; } | (tr -d '\n' && echo "") > /reverse/proxy/white.list
If you had the idea to keep the whitelist up to date, because it is a dynamically allocated client, a cronjob would be suitable to keep the file fresh. So run:
sudo crontab -e
and add the following line if a daily run at 23:30 makes sense for you
30 23 * * * root /here/are/scripts/thewellknownclient-ipv6.sh
6. Adjust your file permissions and restart services
sudo chmod 700 /here/are/scripts/openVPNusers.sh sudo chmod 700 /here/are/scripts/thewellknownclient-ipv6.sh sudo systemctl restart openvpn.service sudo systemctl restart cron.service